Today's #TipTuesday is a continuation of last week's first post on Two Factor Authentication, 2FA for short. Today I am not getting into examples, as I found an interesting article last week after posting my first blog, that illustrates some of why 2FA and password managers are important. Instead of trying to document what already exists, I focused on some other things in this post and ended this with where to get setup information for some common sites.
App Passwords
One thing I forgot to mention last post is the concept of App Passwords comes in once I turn on 2FA, for some software. I was reminded of it while going back through the 2FA setup for Twitter.
Once I turn on 2FA on some sites, there are situations where the desktop software or third-party applications may not be able to handle that. For instance, Skype for Business requires an app password for my Office 365 login so I have to set up an App password in Office 365.
An App password is a specific password that will work for an application when 2FA is not an option. I believe Microsoft recommends setting up an app password per device not per site/software, which I have followed for Office 365 for instance, I set up one App Password for each device where I have software - phones, tablets, and computers. I need it for Skype for Business for sure, but have lost track of where else I need it. I used to require it on the Office install on my computer but I believe I no longer need it there, as my computer "domain" is the Azure AD domain of the O365 tenant I use.
I won't get into more than that, other than users may find this to be a pain in the butt at times as most software won't tell me "Hey, use an app password for this login". Like Skype4Business above, multiple times I will try my regular O365 login thinking I'm typing it in wrong before remembering it needs an app password. Just like the recovery codes mentioned in my first post, I have an app password per device saved somewhere I can access it easily when I need it.
Smart Home Automation Security
I stumbled across an article/video on CBC.ca where the CBC show Marketplace did an investigation into smart home technology and security around it. They hired "white hat" hackers (aka ethical hackers) to test one family's security (with that family's permission for the show). For that family and many others reading or viewing this, it was quite the eye opener where the conveniences of these devices may come at a cost to your privacy if they are not properly secured. That shouldn't be a surprise to people, but it still is.
For the TL;DR crowd or if the article link ever becomes dead, the short version of it is this:
- The target family has several smart home devices (lights, thermostat, security system, front door locks), as they like "knowing what's going on in my house when I'm away" as well as the convenience of an automated home, "for some of the simpler things" like when your hands are too full to turn the lights on.
- The hackers used a sophisticated phishing email to trick one of the homeowners into giving them her login details for the "home hub" software they use to control lights and the front door (Wink). In getting the password via the phishing attack, the hackers were able to unlock the front door and enter the house.*
- The password they used for that site was the same password used for others, like their thermostat and security camera site (Nest), allowing the hackers to control the cameras and view what's happening inside the home.
- In turn, that gave them the ability to send voice commands to the home automation device they used (Amazon Echo) where they could then potentially place orders using the homeowner's stored credit card information.
Mistake #1 - Password Re-use
The family was using the same login and password combination for their Wink hub as they were for their Nest login. "What not to do" - especially around anything where security is important - do not use the same password for two different purposes.
If I want to automate my home and I am including my front door locking mechanism on that (or my garage door or gate system), why on earth would I use either a simple password or the same password for that as something else in my home? People want simplicity, and often that's why they are automating home functions in the first place. I can have simplicity via automation while still ensuring some reasonable risk reduction in my privacy.
Use a password manager to store passwords. Many are free. Many work on multiple devices so users can use it on a home computer and on a mobile device so the passwords stay in sync.
Mistake #2 - not enabling 2FA if it was an option
If either of the sites where the hackers gained access had been enabled with 2FA, this might not have happened. See below in my Reality Check section where there is a big caveat to that statement as 2FA does not prevent hackers from accessing details, it merely reduces the risk.
If 2FA isn't an option with those device vendors, hopefully, they offer security questions as a "something you know" alternative to 2FA. Neither of the banks I deal with offer 2FA so security questions are the only option to secure those sites for me.
Not all sites offer the option for 2FA but many have alternatives that are helpful - like security questions to prove who I am. This site lists all sites that do offer 2FA, for what it's worth. Be aware of which sites should have more security rather than less - like home security, banking, sites storing credit card info etc.
If I were using security questions, I would try hard not to select the easy questions where simple searches are going to find out the answers (my mother's maiden name, my high school, the city I was born in). Instead, look for things that are harder to guess unless the information has been shared on a social media profile (favourite movie, favourite meal, favourite vacation destination etc.). None are foolproof. Think about what information on social media profiles is public, whether those are settings that can be hidden for privacy or whether those are things to avoid using as answers to security questions. Those who regularly post about their beloved "Fighting Bulldogs", using "High School or College Mascot" as a security question should probably be avoided!
Mistake #3 - falling for a phishing email
It's perhaps kind of cruel for me to classify this as a mistake, but it is. Being aware of the possibilities of the places where hackers could target me is important in this day and age. We've all heard of phishing attacks for banking information and home security devices are another ripe target. Being aware it could happen is key, and critically evaluating any alerts is then the priority to avoiding being tricked by a phishing email.
Watch the URL, the entire URL up until the first slash if there is one (and there often is with URLs embedding tracing information, source site info or page/search references). Learning to properly decipher a URL to visually verify it is important. The most common ways phishing attacks work is they either misspell the URL ever so slightly so they count on people not noticing the error or they have a URL which includes part of the real URL in it (and it becomes so long they don't notice the entire URL is a fake).
Example 1: "mybank.com" might be the real URL but a fake could be "mybank.co" or "mybonk.com", hoping a user won't notice the .co/.com distinction or mispelling.
Example 2: same example but with "mybank.com.thisisascam.org" or things like this. Don't just look for "mybank.com" and think "This is right". If there is anything after that other than a "/", it's a sign it might not be real. Something like "mybank.com/?post=2423sfa;fasjf3adsfs" or other super lengthy URLs, that stuff after the slash is generally fine, it's the stuff between the https:// and the next slash is the core URL to be concerned is correct. Many URLs have super long trailing characters for many legitimate reasons. It's not the length of the URL that is the concern, it's the core website named in the URL that is.
Watch out for things like the above examples. On mobile devices, this is often even more of a concern, because "full workstation" techniques like hovering over the URL to preview it don't always work on a mobile device in quite the same manner. Mobile device browsers often hide part of the URL due to screen size limitations.
If I get an email that I find odd, out of place, or not making sense, I will wait to look at it when I am on a regular computer or something with a larger screen. Security is important, and even if the alert seems urgent, that's often the exact scam that hackers rely on to trick users into reacting right away when they should be stopping to check what they are getting into is real.
Reality Check
* In this particular example from Marketplace where the phishing attack occurred, the homeowner thought she was logging into the home hub software and that's how the hackers got the login & password details. If 2FA had been enabled on the site, she wouldn't have received a 2FA secondary login alert (since it was a fake site made to look like the real one). That potentially might have been enough to warn her that something was wrong.
Even under that circumstance, had she enabled 2FA and recognized that she didn't get the secondary authentication alert, the hackers would still have her information at that point, and her house would still be at risk until she changed her password (and also ensured her house was secure). This is what I meant above by 2FA not being the solution to all hacking concerns.
In this example and real-life everywhere, it's likely that this attack would have occurred anyway, even with 2FA applied. Why? Depending on how often I log into this home hub, I may or may not remember I had 2FA applied to it unless I have a personal privacy policy of ALWAYS putting 2FA on these kinds of things. The lack of a 2FA alert may not have been obvious at the time of the alleged phishing incident. "Not" getting an alert for 2FA requires awareness that I should have had an alert in the first place.
The homeowner's comment about the first thing they would do after finding all of this out was "take the door lock off the WiFi". It is relatively far from the first thing I would be doing! I would be focusing on changing passwords, enabling 2FA, and using unique passwords for every site via a password manager.
Conclusion
What's interesting to me is that I was thinking to myself: could this happen to me? I'm pretty confident I'll never fall for a phishing attack. I get enough of them (good and bad ones), plus regular education via ongoing cyber-security training at work, that I'm pretty alert about how one could be fooled. I've also used 2FA for so long that there are many websites where I log in and automatically pick up my phone just waiting for the alert or prompt to complete the login process. It's second nature to me. If I don't get one, I would wonder what happened.
The thing is, on obscure sites that I don't log into every day, I don't necessarily remember which ones have 2FA on them and which don't. So many sites don't offer that or didn't last time I checked that it's very easy to lose track.
How do I protect myself?
Use a password manager
I use LastPass but many other vendors have excellent apps. I like the feature it has where I can do a Security Challenge to have it check my sites and how I'm doing from the standpoint of security. Do I reuse many passwords? How many are statistically not very complex? I have 208 sites/passwords stored in here as I write this, and 7 are duplicated and 1 is marked as weak. Those are easy to address. 16 passwords have a strength rating of less than 90% and many of those (other than the 8 weak or duplicates) are due to the sites themselves not allowing long enough passwords to be truly strong. I went through the painful exercise several months ago of reviewing every single duplicate or weak password and changing most of them to individual randomly generated ones. It took me months to complete and was mind-numbingly boring, but I feel a lot better now about my risk levels.
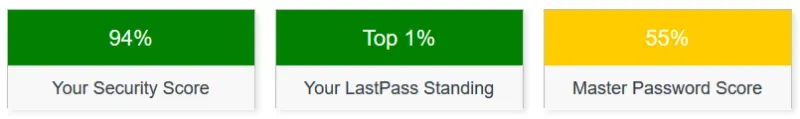
Oddly enough this one doesn't like my master password, which is because I chose to use a passphrase, not a complex password. A passphrase is a bunch of random words that collectively mean nothing (as in, they don't form a sentence) but they are "regular" dictionary words which LastPass doesn't like. I do plan on changing that probably yearly just to keep it fresh and updated as well.
Enable password re-prompt
This is a LastPass feature but I'm sure other password managers have a similar feature as well. On certain key sites that I have concerns with, I turn on a password-prompt flag. Every time I log into that site via the password manager, it will re-prompt me for my master password.
I do this because I know I've been inconsistent with the settings on the various computers I use LastPass on. On some I've turned on "remember the master password for x days" and on others, I have prompting me as soon as I open the browser. I don't want to be in a situation where my computer is physically compromised and all of a sudden they can log into my bank because my master password is "saved". I just haven't taken the time to make all of those settings consistent (which would be to remove any "save for x days" option!).
Careful with Security Questions
On sites where I can't enable 2FA, which has a security question option, I will use it and I will generally mark the box to "require security questions on this device" so I'm prompted each time, even though it delays my login slightly. I share a fair bit of personal information in my blogs and on my Twitter feed, so I am extremely cautious of what I use for security questions and answers! Sometimes the options are way too limited and there is no choice but I pick the most obscure things from the lists or, at times, provide fake information that only I would remember. For example: what is my dog's name? I might answer that even though I don't have and have never had a dog, I'll use a good friend's dog's name as the answer.
Don't save passwords in the browser
One of the first things I do on any new machine, on every browser, is to disable the saving of passwords, as that is why I have a password manager. I don't want the browser also saving that information. On some sites, I ensure I never mark the option to "remember me", where I don't want someone unauthorized to log in to that site. If I share a computer or others can access it "as you" (like an IT department), think about it before ticking that box. On some sites like a user forum for a piece of software, sure, who cares if it saves a cookie but on your banking? No way.
Ignore games & surveys on social media
Facebook in particular is famous for viral posts and games. "Let's have some fun getting to know each other" with a bunch of questions users are supposed to copy and paste and answer on their feed, sharing with all of their friends. Cool right? Well, sometimes yes and sometimes no. Think about the things that are being answered and think about the security questions that are on sites offering that basic level of two-factor security. How similar are they? Honestly, those posts would make excellent sources of security questions!
Someone in my family recently posted something along those lines - on a public post anyone could see. It was even worse than the "get to know each other" ones: where were their parents born, what were their parents' maiden names, what were their parents' maiden names etc. OMG. Needless to say several people posted right away to take it down and expressed their concerns over obliviously sharing that kind of information publicly. The biggest problem I have with something like Facebook is so much of the security is only as good as contacts’ and friends’ security. I don't have anything on my FB profile public other than what I have no choice in, but it's easy to find who I'm friends with if I find someone else who does make that public, and I can do nothing about it.
There are also meaningless surveys which I'm always concerned about who is behind the information. "What kind of animal would I be?" or things where I answer a bunch of personality quiz type of information and they spit out some canned profile based on what I answer. I have no idea who is behind those things nor do I trust them with that information!
Next Steps
Here are some links on how to set up 2FA on various common sites. I was going to go through all of the steps myself again on each one but it started taking a ridiculous amount of time to document something that is already out there! Besides each, I've listed what methods they offer as of writing this blog.
- Twitter (SMS, Hardware or Software token)
- Facebook (SMS, Hardware or Software token)
- Google (SMS, Phone Call, Hardware or Software token)
- Office365 (SMS, Phone Call, Software token)
The links for the above are from the Two Factor Auth List and there are plenty more sites with the info for those sites not listed above.

