Back in October last year, I posted a couple of articles around my recommendations and use of Two-Factor authentication. (Here’s part 1 and part 2 for those articles.)
In my part 2 post, I indicated that I was also using a password manager and was using LastPass at the time. I have recently switched to 1Password and after posting a couple of things about that on Twitter, a few friends and followers expressed interest in knowing more about why I switched and how I would compare the two of them.
Brief background
I used Roboform for many years but started finding it feeling a bit clunky. Yes, I realize that is completely useless as any viable feedback about a product, but that’s how I can phrase it. I just found the UI “tired” and was looking for something new.
So, about a year ago, I made the switch to LastPass. I wish I could remember more of my reasons for changing but I can’t any longer, they’re gone from my memory! LastPass appeared to have some features that Roboform didn’t (at the time, at least) so that’s what I chose. It’s quite likely that what I liked about LastPass is in the Roboform product today for all I know, as the “good” password manager products out there do keep adding new features to their products. I do consider all 3 products I’ve used to be good, I just now prefer 1Password.
Why did I switch?
When I switched to LastPass, I looked at 1Password too at that time and, to be honest, I liked that LastPass had an “always free” version where 1Password only had a 30-day trial (after which it was a paid product). Fast forward to the present day, and I’ve learned more about infosec generally in the last year (out of interest) and decided to make a change.
My (somewhat lame) first reason
The more I read about data breaches and infosec news, the more I am subscribing to the theory that “if you’re not paying for the product, YOU are the product”. This isn’t the “real” reason I changed, as I could have simply upgraded to a premium version of LastPass. It was just one of the things that made me re-think my decision as cost was a factor a year ago when I don’t think it should have been.
The key reason: integration with Have I Been Pwned
LastPass has a “security center” feature which, among other things, checks if any of the logins were compromised (in a data breach). 1Password takes this to the next level, in my opinion. It integrates with Have I Been Pwned (HIBP for short, Troy Hunt’s service around data breaches) in its Watchtower feature, in two ways:
- Check logins against the HIBP service to see if they’ve been in a breach. LastPass does the same thing, although I’m unsure if it uses HIBP.
- Check passwords against the HIBP’s Pawned Passwords service to see if they have been found in a breach.
I was specifically interested in the second feature above. I already subscribe to HIBP’s feature that will send me an email when one of my accounts is in a data breach once they become aware of it. I typically use only one email address that is only for logins, not for friends, family or other correspondence. Oddly enough, in the 15-20 years I’ve used this as a login, it’s only been in one known breach and that was the most recent one called “Collection #1”. That’s simply good luck, nothing I can claim I’m doing to avoid that situation. My business email was in the LinkedIn data breach years ago, which is an example of a site where the random login email account wouldn’t have been appropriate for business communications, and I’ve paid for that by it being in a breach and is on lists in god-knows-where on the deep dark web.
I have taken the time to ensure that nearly every site I use has its own unique, randomly-generated password so what I’m interested in watching for now are instances where those passwords have been in a data breach. I’ll describe more below about how this works as it sounds like “they’re sending my passwords over the internet?”. No, they’re not. Now that I’m confident most of my logins are adequately secure and complex if any of those appear in a data breach, I will know exactly what site it might have come from as my sites:passwords are a 1:1 relationship. If one of those passwords is in a breach, it doesn’t necessarily mean MY account was in the breach (others may have the same randomly generated password), but the odds are it’s mine and I can go to that site and change my password.
Troy Hunt and HIBP
I have followed Troy Hunt on Twitter since I became a Microsoft MVP (when I first became aware of him). Troy is a fellow Microsoft MVP as well as a Microsoft Regional Director. He is the creator of the incredibly useful Have I Been Pwned service.
After listening to him speak as well as getting a chance to meet him last year at MVP Summit, I have taken an even more keen interest in infosec. As I have listened to his weekly podcasts over the past year, I realized I still have a lot to learn about it.
His HIBP service is a free service, which originally started with checking if an email account was in a data breach. Here’s a clip of the stats from the landing page about what’s in his databases at the moment.
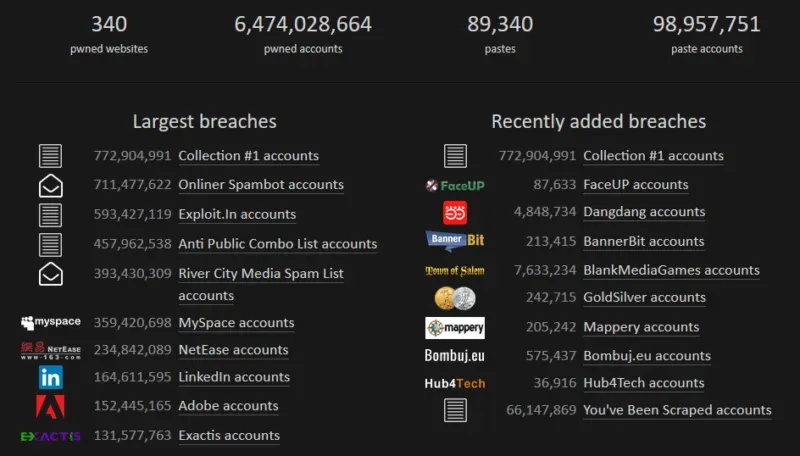
The key takeaway that is important to note here is the pawned logins are not stored along with the pawned passwords. If my email is in a data breach, there is no service where he tells me which password they used in that breach. Lots of people argue with him over that but the reasons are clear, and he’s blogged about it here.
The Pawned Passwords feature is interesting to me on a level where I don’t entirely understand the technical details but understand the concept. In 1Password, the passwords are hashed (not stored in plain text for anyone to read/see) and the service to check against the HIBP passwords feature sends the first 5 characters of the hash to HIBP’s API and it returns all of the hashes that match that prefix. 1Password then compares my hash to the list returned to see if I’m in it. No passwords are passed back and forth. Part of the hash is sent back and forth but not the whole hash so only the sender/receiver knows the full hash to be able to know the full password at any given time.
His example is this: let’s say I have “P@ssw0rd” in my list. The hashed value of that is “21BD12DC183F740EE76F27B78EB39C8AD972A757”. 1Password sends “21BD1” and HIBP returns (at the time he wrote this example) 475 results, for the items that start with “21BD1”. If “2DC183F740EE76F27B78EB39C8AD972A757” is in that list, then the password is flagged as compromised. More details about this example are in this post.
Comparisons
Things I prefer in 1Password
It’s a bit too early to do a LOT of comparing but already I’m seeing things I like a lot better in 1Password than LastPass. Here’s the Watchtower “menu”:
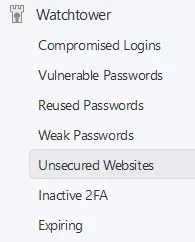
To be fair, both products have features around re-used passwords, weak passwords and compromised logins. I described above why I was interested in the vulnerable passwords feature. I like the bottom 3 features as well, which I don’t recall an equivalent of in LastPass: insecure websites (HTTP not HTTPS), sites which have 2FA options that I’m not using and expiring passwords. I’ve already used the unsecured websites feature to update all of my URLs if the site was using HTTPS. Most were, but the old password manager happened to just have whatever site I saved at the time, many were the HTTP version.
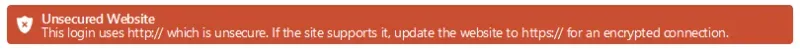
This (above) is what appears on the Unsecured Website area or if I’m on a site where my login is in that list. It will not let me auto-fill that login or password (or so it seems). That I find a tad annoying. I’m fine being alerted to the issue but if the site isn’t secure and there is no option, I would prefer if it auto-filled my login and password for me anyway.
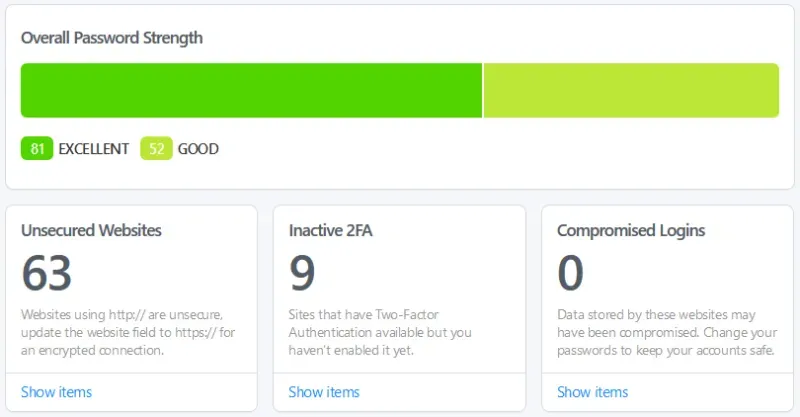
This is a snapshot of one of my vaults. Today the Unsecured Websites number is 2, which are both things I can’t change. I have several sites where I can enable 2FA, so that’s my next target. I don’t have any compromised logins, weak passwords or vulnerable passwords so that’s a good thing.
Another thing I noticed that I like is the choice of type of random password generation, other than the typical length and whether to include numbers or symbols. 1Password gives users a “memorable password” option which sounds dumb on the surface, but it’s helping create passphrases that will be better and easier to remember while still being lengthy enough to be a security improvement.
Lastly, I like that I can have different “vaults” – groups of saved logins etc. I can segregate ones for work from personal ones and have created a vault for sites I no longer use, but want to keep the details in case of future data breaches. That keeps my active login list a lot smaller and more manageable.
Similar features are implemented in different ways
Various sites I subscribe to have different URLs but the same login and password. Amazon.com and .ca for instance. GPUG.com and all of the other UGs are another example. The way these work in LastPass is via an “Equivalent Domains” feature which is a place where I can say “Amazon.com and Amazon.ca are equivalent domains”. That allows me to have 1 login saved and thus avoids the “there are 2 logins with the same password” problem.
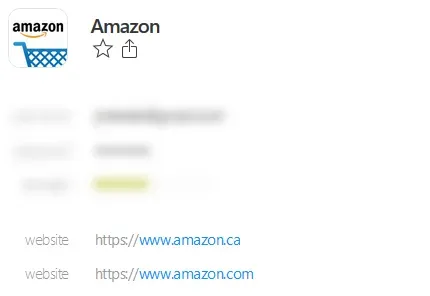
In 1Password it appears that on a login, I can list different URLs which is a different way of implementing the same feature. I quite like this because I can also label it if I need to, other than each being called “website”. I didn’t, in the example above, but I could label them Canada, USA or whatever makes sense for the different sites using 1 login/password combination. In this case, they are linked so I can’t have different logins for the sites. If I have a choice not to use the same login & password combination, I would rather do that and separate the logins. Some sites are related but utilize the same authentication in the back end so I don’t have that choice.
One LastPass feature I’ll miss
The one feature I’ll miss that I can’t find on 1Password was something I don’t know the name of but I could lock some passwords in and require that I re-type my password if I used them. I put that on my banking sites, anything work-related, and anything with financial info saved (sites with credit cards I can’t remove) and things like that. If that’s available in 1Password, I’ve yet to find it. It was a nice 2nd layer to force me to authenticate a 2nd time before using that particular login.
Last thoughts
That’s pretty much it for this post. I think what I may do for a #TipTuesday is write a brief primer on how to get started with using a password manager. There are lots of people who don’t use one and use far less secure ways of tracking their passwords, either in an unsecured note on their phones or computers or even worse, re-use passwords to reduce what they have to remember. A password manager and working through logins to re-generate passwords to be more complex is a much safer, better alternative!